Fort Knox for Your Data!
Imagine a place where your most valuable possessions are kept safe and secure. A place where the highest level of security measures are in place to protect your treasures from any potential threats. This place is like Fort Knox, the famous United States Bullion Depository, which houses a vast amount of gold and other precious assets. But what if I told you that there is a digital equivalent of Fort Knox for your data?
Enter Public Key Infrastructure (PKI), the modern-day Fort Knox for your data. PKI is a system that uses digital certificates and encryption techniques to secure communications and authenticate users in the digital world. Just like Fort Knox is heavily guarded and protected, PKI employs robust security measures to keep your data safe from cyber threats.
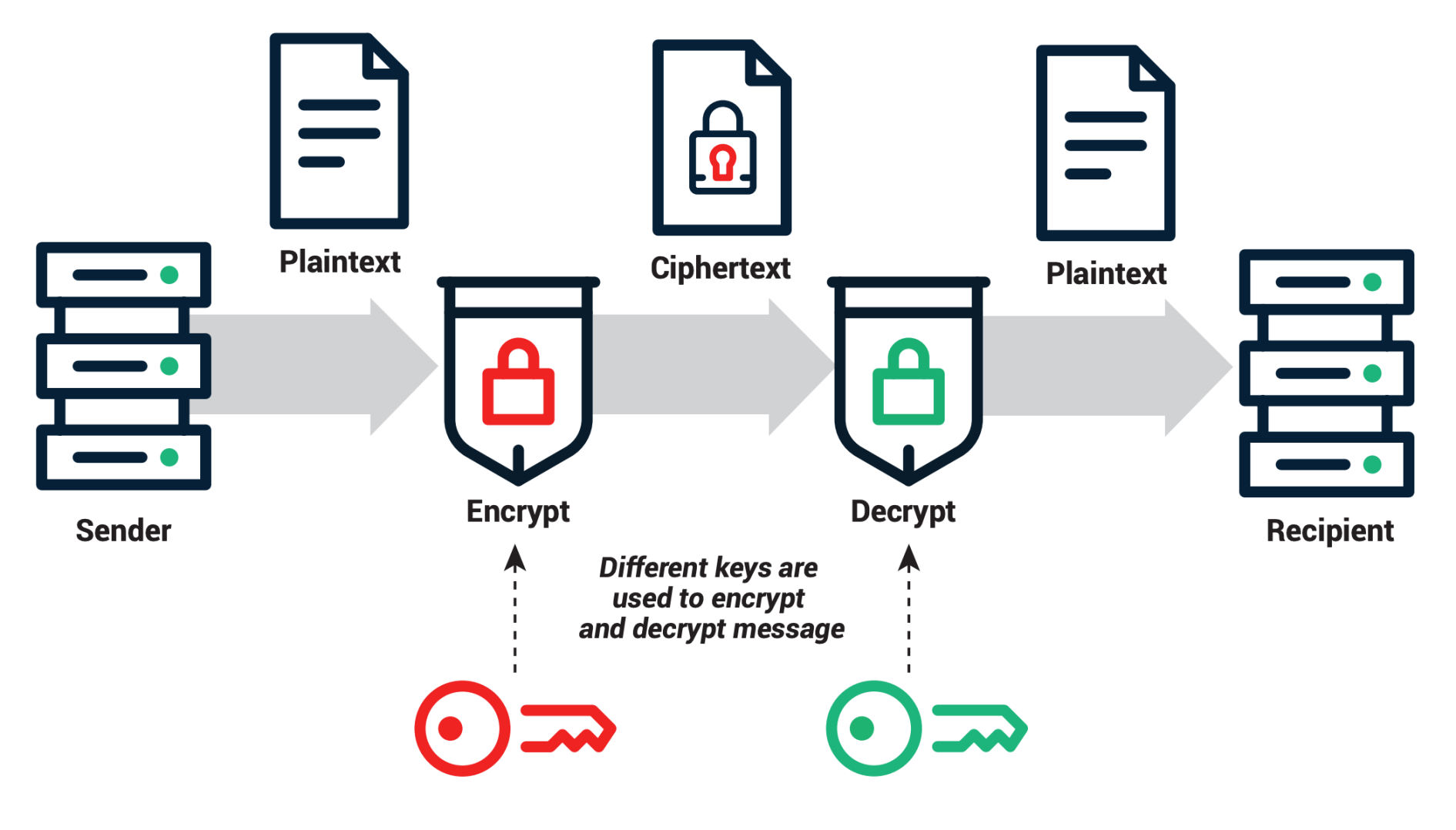
One of the key components of PKI is the use of public and private keys. These keys work together to create a secure communication channel between parties, ensuring that data is encrypted and secure from prying eyes. The public key is freely available to anyone who wants to communicate securely, while the private key is kept secret and known only to the owner.
When you send a message or data using PKI, it is encrypted with the recipient’s public key, ensuring that only they can decrypt and read the information with their private key. This process ensures that your data remains confidential and secure, much like the gold bars locked away in Fort Knox.
But PKI is not just about encryption. It also plays a crucial role in authentication, ensuring that the parties involved in a communication are who they claim to be. Just like you would need to show identification to gain access to Fort Knox, PKI uses digital certificates to verify the identity of users and devices in the digital realm.
These certificates are issued by trusted Certificate Authorities (CAs) and contain information about the owner, their public key, and the validity period of the certificate. By verifying the digital certificate, recipients can be confident that the sender is legitimate and that the data has not been tampered with during transmission.
In addition to encryption and authentication, PKI also provides a mechanism for non-repudiation. This means that once a message has been sent and signed with a private key, the sender cannot deny sending it later on. This feature ensures accountability and helps to prevent fraud and disputes in digital transactions.
So, how does PKI keep your data safe, much like Fort Knox? By employing a multi-layered approach to security that includes encryption, authentication, and non-repudiation, PKI ensures that your data is protected at all times. Just like the gold bars in Fort Knox are safeguarded by layers of security, your digital assets are shielded by the robust security measures of PKI.
In conclusion, Public Key Infrastructure acts as the modern-day Fort Knox for your data, providing the highest level of security and protection in the digital world. By using encryption, authentication, and non-repudiation, PKI ensures that your data remains confidential, secure, and tamper-proof. So next time you send a sensitive message or conduct an online transaction, rest assured that PKI is working behind the scenes to keep your data safe and sound.
The Power of Public Key Infrastructure
Imagine sending a secret message to a friend. You want to make sure that only your friend can read it, and no one else can intercept or decipher it. This is where Public Key Infrastructure (PKI) comes into play, acting as a digital security system that ensures the confidentiality, integrity, and authenticity of your data.
PKI is like having your own personal Fort Knox for your data, providing a secure way to communicate and exchange information over the internet. It is a sophisticated encryption technology that uses a pair of cryptographic keys to secure data transmissions. These keys are known as the public key and the private key.
The public key is shared with anyone who wants to communicate with you securely. It is like a lock that others can use to encrypt messages that only you can unlock with your private key. The private key is kept secret and known only to you, allowing you to decrypt messages that have been encrypted with your public key.
One of the key benefits of PKI is that it provides a secure way to authenticate the identity of users and devices. When you receive a message encrypted with someone’s public key, you can be confident that it was sent by that specific individual or organization. This helps to prevent impersonation and ensures the integrity of the communication.
PKI also plays a crucial role in ensuring the confidentiality of data. By encrypting messages with the recipient’s public key, you can be sure that only the intended recipient can read the information. This is especially important when sending sensitive data, such as financial information or personal details.
Additionally, PKI helps to maintain the integrity of data by ensuring that it has not been tampered with during transmission. By using digital signatures, PKI can verify that the sender of a message is who they claim to be and that the message has not been altered in any way.
In today’s digital age, where cyber threats are constantly evolving, PKI is essential for keeping your data safe and secure. It provides a robust defense against unauthorized access, interception, and manipulation of sensitive information. With PKI, you can communicate with confidence, knowing that your data is protected.
So, the next time you send a message to a friend, think about the power of Public Key Infrastructure working behind the scenes to keep your communication secure. Just like Fort Knox protects valuable assets, PKI safeguards your data, ensuring that only the intended recipients can access and understand your messages. Unlock the security of PKI and enjoy peace of mind knowing that your data is safe from prying eyes.



