Ready to Level Up? Test Your Security with Penetration Testing!
Are you ready to take your security to the next level? It’s time to put your defenses to the test with penetration testing! This cutting-edge practice involves simulating cyber attacks to identify vulnerabilities in your systems before real hackers can exploit them. It’s like having a friendly hacker on your side, helping you uncover weaknesses and fortify your defenses.
Penetration testing, also known as pen testing, is a crucial tool in the fight against cyber threats. By proactively identifying and addressing vulnerabilities, you can prevent costly data breaches and protect your sensitive information. It’s like a security audit on steroids, giving you valuable insights into the effectiveness of your security measures.
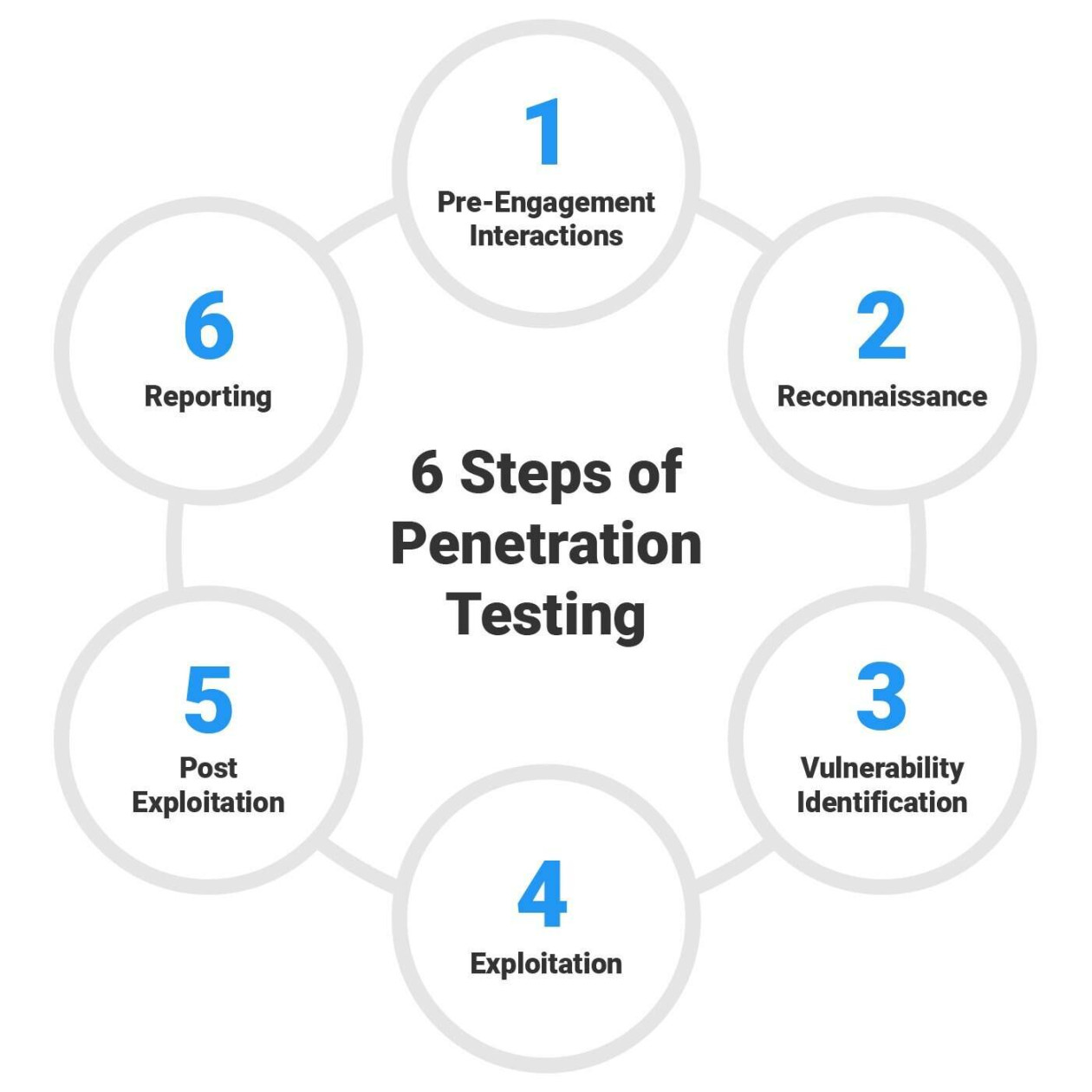
So how does penetration testing work? It starts with a team of skilled ethical hackers, also known as penetration testers, who use a variety of tools and techniques to probe your systems for weaknesses. They might try to exploit known vulnerabilities, use social engineering tactics to trick employees into revealing sensitive information, or launch sophisticated attacks to test your defenses.
But don’t worry, these ethical hackers are on your side. Their goal is to help you improve your security, not to cause harm. Think of them as friendly neighborhood superheroes, swooping in to save the day by uncovering hidden dangers and shoring up your defenses.
One of the key benefits of penetration testing is that it allows you to see your security posture from the perspective of a real attacker. By thinking like a hacker, you can better understand where your weaknesses lie and take proactive steps to address them. It’s like playing a game of cat and mouse with cyber criminals, staying one step ahead of their every move.
Penetration testing can also help you comply with regulatory requirements and industry standards. Many regulations, such as GDPR and PCI DSS, require organizations to regularly test their security measures to protect customer data. By conducting penetration tests, you can demonstrate due diligence and show that you take security seriously.
But penetration testing is not just about meeting regulatory requirements – it’s about protecting your business and your customers from cyber threats. In today’s digital world, data breaches can have devastating consequences, both financially and reputationally. By investing in penetration testing, you can stay one step ahead of cyber criminals and keep your sensitive information safe.
So, are you ready to level up and test your security with penetration testing? It’s time to unleash your inner hacker and see your defenses in action. Don’t wait until it’s too late – take proactive steps to protect your business and safeguard your sensitive information. With penetration testing, you can stay one step ahead of cyber threats and keep your security strong.
Unleash Your Inner Hacker: Get a Sneak Peek with Pen Testing!
Have you ever wondered what it would be like to be a hacker, breaking into systems and uncovering vulnerabilities? While hacking is illegal and unethical, there is a legal and ethical way to satisfy your curiosity – through penetration testing.
Penetration testing, or pen testing for short, is a simulated cyber attack on a computer system, network, or web application to uncover security weaknesses. It is a proactive way for organizations to identify and fix vulnerabilities before malicious hackers can exploit them.
So how can you unleash your inner hacker and get a sneak peek into the world of penetration testing? Here are some tips to get you started:
1. Learn the Basics: Before you can start pen testing, you need to understand the basics of hacking and cybersecurity. There are plenty of online resources, courses, and tutorials available that can help you learn about different hacking techniques, tools, and methodologies.
2. Set Up a Lab: To practice your pen testing skills, you can set up a virtual lab environment using tools like VirtualBox or VMware. This will allow you to create a safe space to test different hacking techniques without causing any harm to real systems.
3. Choose Your Tools: There are many pen testing tools available, both free and paid, that can help you simulate cyber attacks. Some popular tools include Metasploit, Nessus, and Burp Suite. Experiment with different tools to see which ones work best for you.
4. Practice, Practice, Practice: The key to becoming proficient in penetration testing is practice. Try hacking into your own lab environment or participating in Capture The Flag (CTF) competitions to hone your skills and learn new techniques.
5. Stay Ethical: It is important to remember that penetration testing should always be done ethically and legally. Never attempt to hack into systems or networks without permission, as this is illegal and can have serious consequences.
By following these tips, you can get a sneak peek into the world of penetration testing and unleash your inner hacker in a legal and ethical way. Who knows, you may even discover a passion for cybersecurity and decide to pursue a career in this exciting field. So what are you waiting for? Get started on your pen testing journey today!



