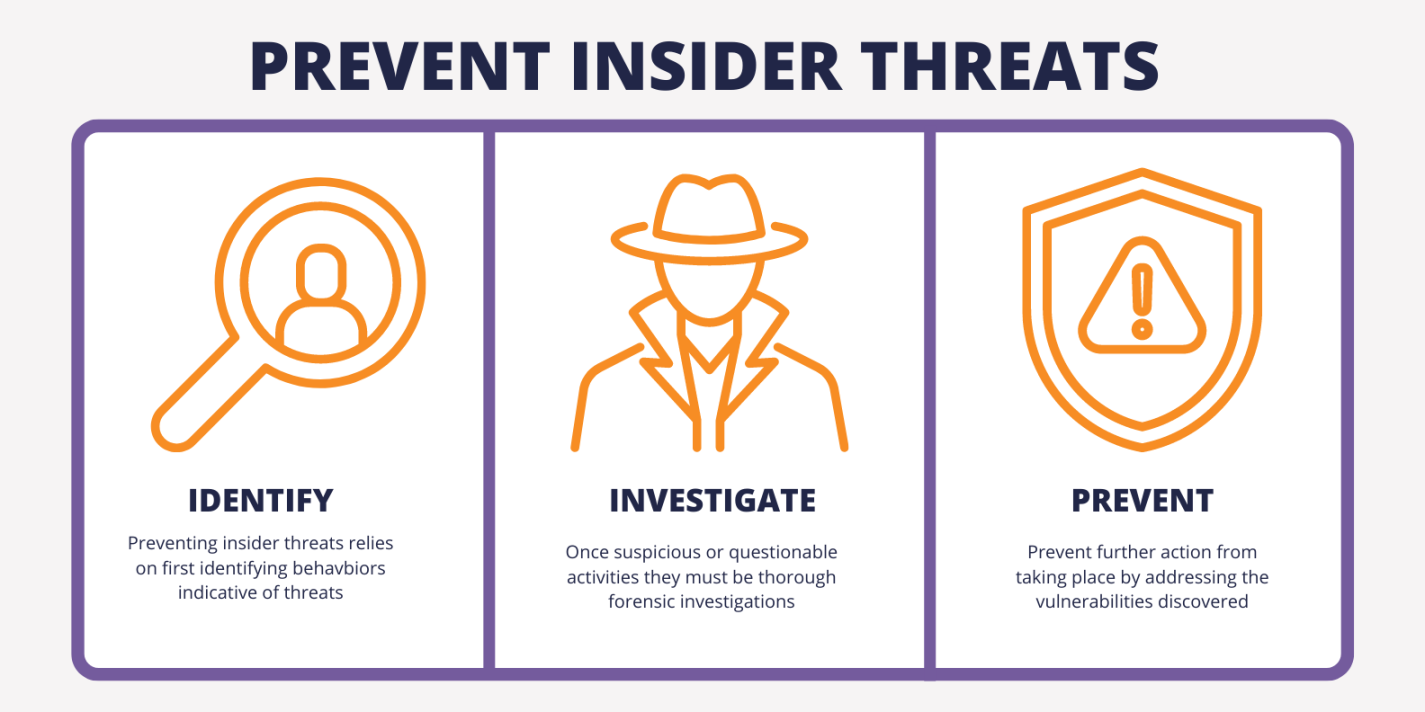
Beware of Hidden Dangers Within!
In today’s fast-paced and interconnected world, it’s easy to focus on external threats and overlook the hidden dangers that lurk within our own organizations. From rogue employees to malicious software, the threats that come from within can be just as damaging as those from outside. That’s why it’s crucial to stay alert and vigilant against these sneaky internal threats.
One of the most common internal threats that organizations face is the threat of insider attacks. These attacks can come from disgruntled employees, careless workers, or even unwitting accomplices who have been tricked into giving away sensitive information. Insider attacks can be incredibly damaging, as the attacker often has intimate knowledge of the organization’s systems and can easily bypass traditional security measures.

To protect against insider attacks, organizations should implement strong access controls, conduct regular security training for employees, and monitor network activity for any suspicious behavior. By staying vigilant and proactive, organizations can significantly reduce the risk of insider attacks and protect their sensitive data.
Another hidden danger within organizations is the threat of shadow IT. Shadow IT refers to the use of unauthorized software, applications, or devices within an organization. This can include employees using personal devices for work tasks, downloading unapproved software, or using cloud services without permission.
Shadow IT can pose a significant security risk, as these unauthorized tools may not have the same level of security controls as approved software. This can leave organizations vulnerable to data breaches, malware infections, and other security threats. To mitigate the risk of shadow IT, organizations should establish clear policies and procedures around the use of technology, provide employees with approved tools for their work, and regularly monitor network activity for any unauthorized devices or software.
In addition to insider attacks and shadow IT, organizations must also be wary of the threat of social engineering. Social engineering is a tactic used by attackers to manipulate individuals into divulging confidential information or performing actions that compromise security. This can include phishing emails, phone scams, or even in-person interactions where an attacker poses as a trusted individual.
Social engineering attacks can be incredibly deceptive and difficult to detect, making them a significant threat to organizations of all sizes. To protect against social engineering attacks, organizations should provide employees with regular training on how to recognize and respond to phishing attempts, establish clear protocols for verifying the identity of individuals requesting sensitive information, and implement multi-factor authentication to add an extra layer of security.
Overall, it’s essential for organizations to be aware of the hidden dangers that can come from within. By staying alert and proactive, organizations can protect themselves against insider attacks, shadow IT, social engineering, and other internal threats. Remember, the best defense is a strong offense when it comes to cybersecurity – so don’t let sneaky threats from the inside catch you off guard.
Stay Alert for Sneaky Internal Threats!
When it comes to protecting our homes, businesses, and personal information, we often think about outside threats such as hackers, burglars, and other malicious individuals. However, sometimes the biggest dangers can come from within. It’s important to stay alert and vigilant for sneaky internal threats that could pose a risk to our safety and security.
One of the most common internal threats is employee theft. Whether it’s stealing office supplies, taking cash from the register, or embezzling funds, employee theft can have a significant impact on a business’s bottom line. It’s important for employers to implement strict policies and procedures to prevent theft, such as conducting regular audits and background checks on employees.
Another sneaky internal threat to watch out for is insider threats. These are individuals within an organization who have access to sensitive information and may use it for malicious purposes. Insider threats can include disgruntled employees, contractors, or even trusted partners who have gone rogue. It’s crucial for businesses to monitor and control access to sensitive data to prevent insider threats from causing harm.
In addition to employee theft and insider threats, another internal threat to be aware of is sabotage. This can come in many forms, such as intentionally damaging equipment, altering data, or disrupting operations. Sabotage can be difficult to detect, as the perpetrator may try to cover their tracks. It’s important for businesses to have security measures in place, such as surveillance cameras and access controls, to deter sabotage and catch perpetrators in the act.
Another sneaky internal threat to watch out for is negligence. This can occur when employees fail to follow proper procedures or ignore security protocols, putting the organization at risk. Negligence can lead to data breaches, accidents, and other costly mistakes. It’s important for businesses to provide regular training and education to employees to ensure they understand the importance of following security protocols.
In addition to employee theft, insider threats, sabotage, and negligence, businesses should also be on the lookout for fraud. This can involve employees manipulating financial records, creating fake invoices, or engaging in other deceptive practices for personal gain. Fraud can have serious legal and financial consequences for businesses, so it’s important to have strong internal controls in place to prevent and detect fraud.
Overall, staying alert for sneaky internal threats is essential for protecting our homes, businesses, and personal information. By being proactive and implementing strong security measures, we can reduce the risk of internal threats and safeguard what matters most to us. Remember, the biggest dangers are not always the ones we can see – sometimes they come from within. Stay vigilant and stay safe!

![What's the Best Authentication Method? Analysis []](https://rusterpedia.biz.id/wp-content/uploads/2024/10/what-s-the-best-authentication-method-analysis-60x60.png)
