Uncover the Elusive: Zero-Day Exploits Revealed!
Welcome to the mysterious world of cybersecurity intrigue, where hidden dangers lurk behind every corner. Today, we are going to delve into one of the sneakiest cyber attacks you’ve probably never heard of: zero-day exploits. These elusive tactics are the stuff of hacker legends, allowing cyber criminals to strike without warning and wreak havoc on unsuspecting victims.
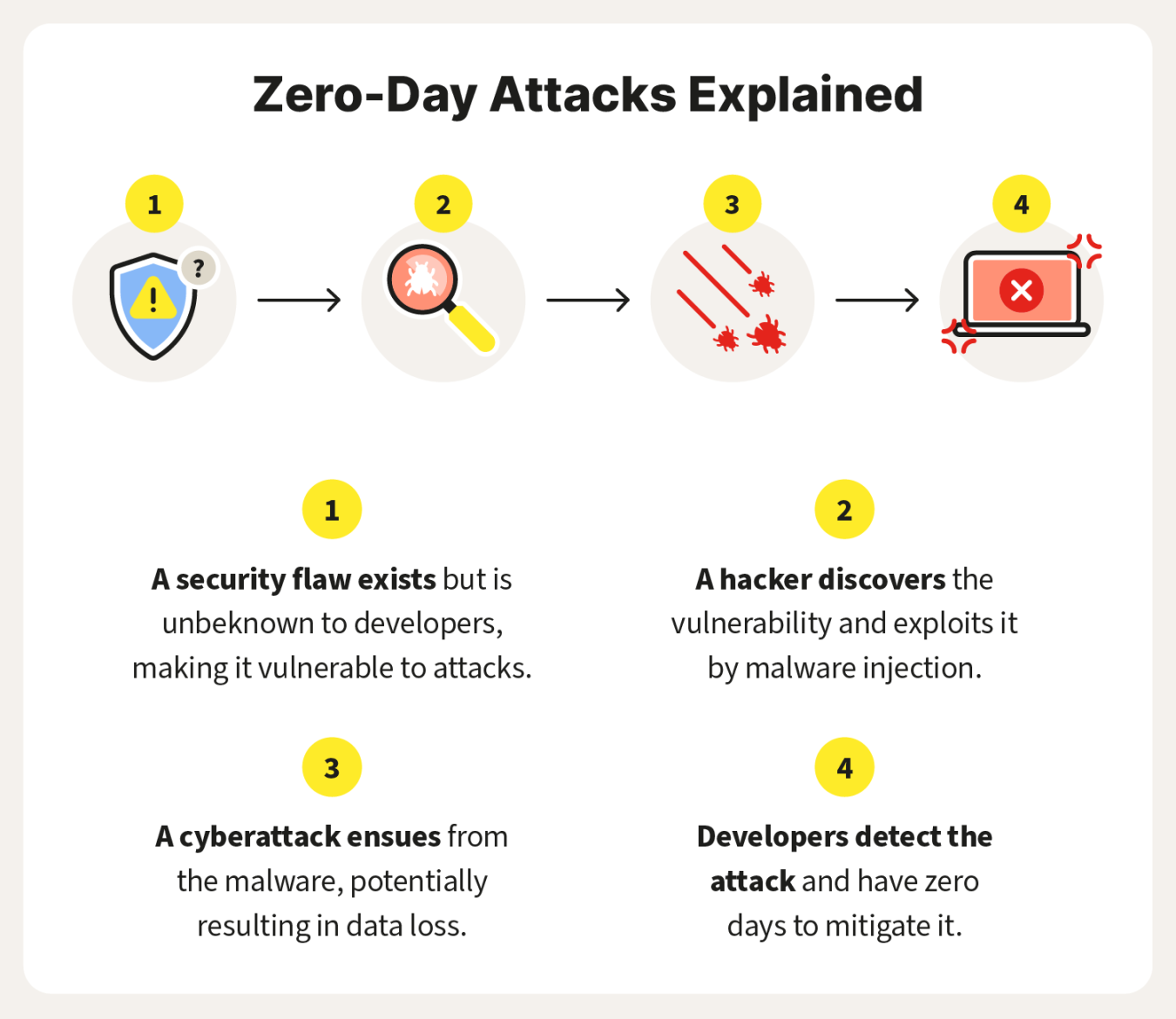
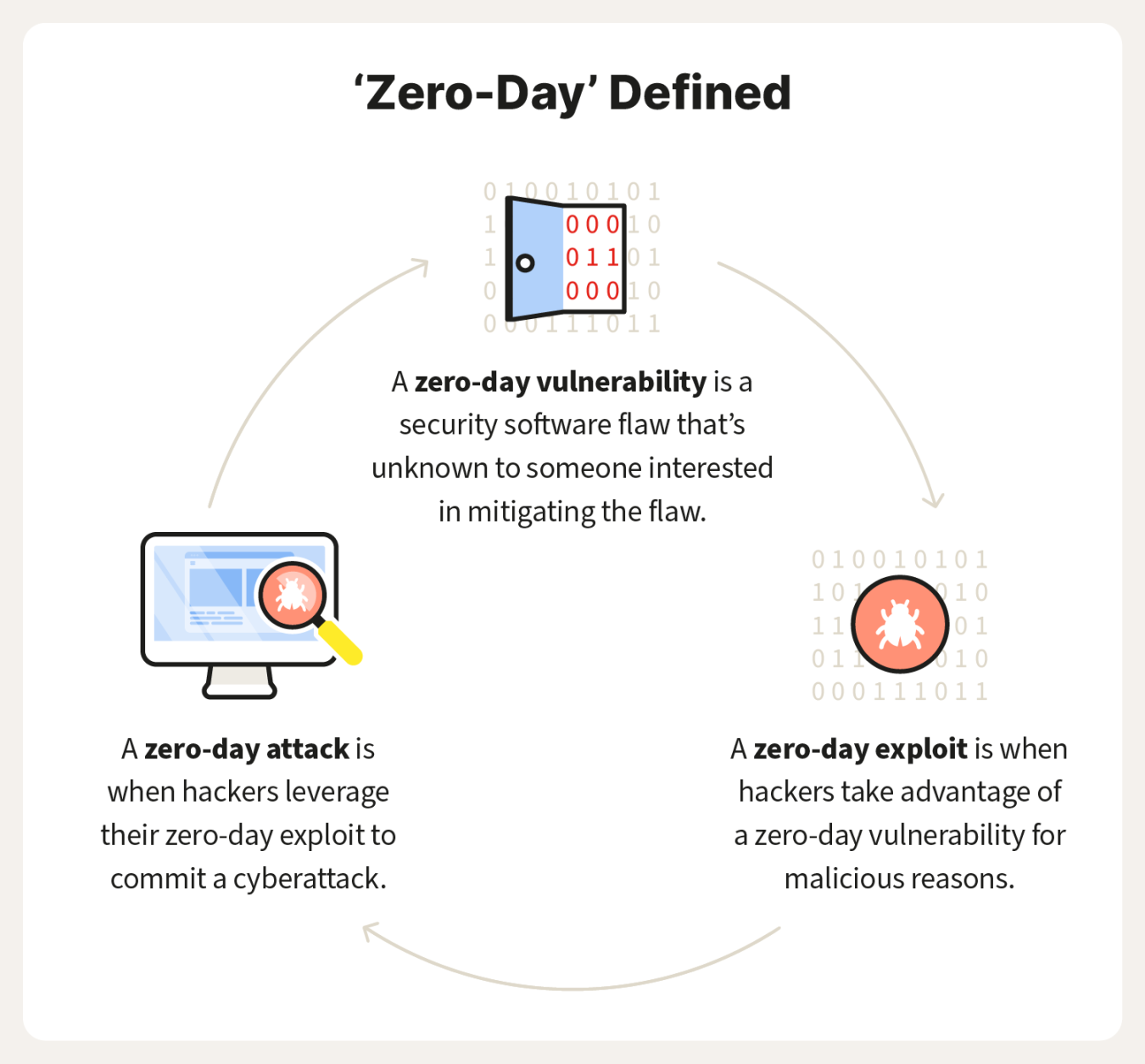
So, what exactly is a zero-day exploit? In simple terms, it is a type of cyber attack that takes advantage of a software vulnerability that is unknown to the developer. This means that the hackers are one step ahead of the game, using their insider knowledge to infiltrate systems and steal sensitive information before the developers even realize there is a problem.
Imagine a burglar who knows about a secret entrance to your house that you didn’t even know existed. That’s essentially what a zero-day exploit is – a sneaky backdoor that allows hackers to slip into your system undetected and cause all sorts of chaos.
But how do these cyber criminals find these hidden vulnerabilities in the first place? Well, it’s a bit like a game of cat and mouse. Hackers are constantly scouring the internet, looking for cracks in the armor of popular software programs. They use sophisticated tools and techniques to identify weaknesses that the average user would never even think to look for.
Once they have identified a potential zero-day exploit, the hackers waste no time in exploiting it for their own gain. They can use these vulnerabilities to steal sensitive data, install malware, or even take control of the entire system. It’s a frightening thought, knowing that someone out there could be lurking in the shadows, just waiting for the right moment to strike.
So, how can you protect yourself from these elusive cyber attacks? The key is to stay one step ahead of the hackers. This means keeping your software up to date, as developers are constantly releasing patches and updates to fix known vulnerabilities. It also means being vigilant about the websites you visit and the emails you open, as these are often the entry points for zero-day exploits.
But even with the best security measures in place, there is always a chance that you could fall victim to a zero-day exploit. That’s why it’s important to have a plan in place for dealing with a potential attack. Make sure you have backups of your important data, so that you can quickly recover in the event of a breach.
In conclusion, zero-day exploits are a serious threat in the world of cybersecurity. These sneaky attacks can cause untold damage to individuals and businesses alike, leaving a trail of destruction in their wake. By staying informed and taking proactive steps to protect yourself, you can reduce the risk of falling victim to these elusive cyber attacks. So, keep your guard up and stay one step ahead of the hackers – because you never know when they might strike next.
Sneak Peek into the World of Cybersecurity Intrigue
Welcome to the thrilling world of cybersecurity intrigue, where hackers and defenders engage in a constant battle of wits and technology. In this fast-paced digital landscape, one of the most elusive and dangerous weapons in a hacker’s arsenal is the zero-day exploit. But what exactly is a zero-day exploit, and how does it work? Join us as we uncover the secrets of this sneaky cyber attack that you’ve probably never heard of before.
Imagine a world where your computer, smartphone, or even your smart home devices are constantly under threat from invisible enemies. These enemies are not human, but rather lines of code written by malicious hackers with the intent to exploit vulnerabilities in your devices. This is where zero-day exploits come into play.
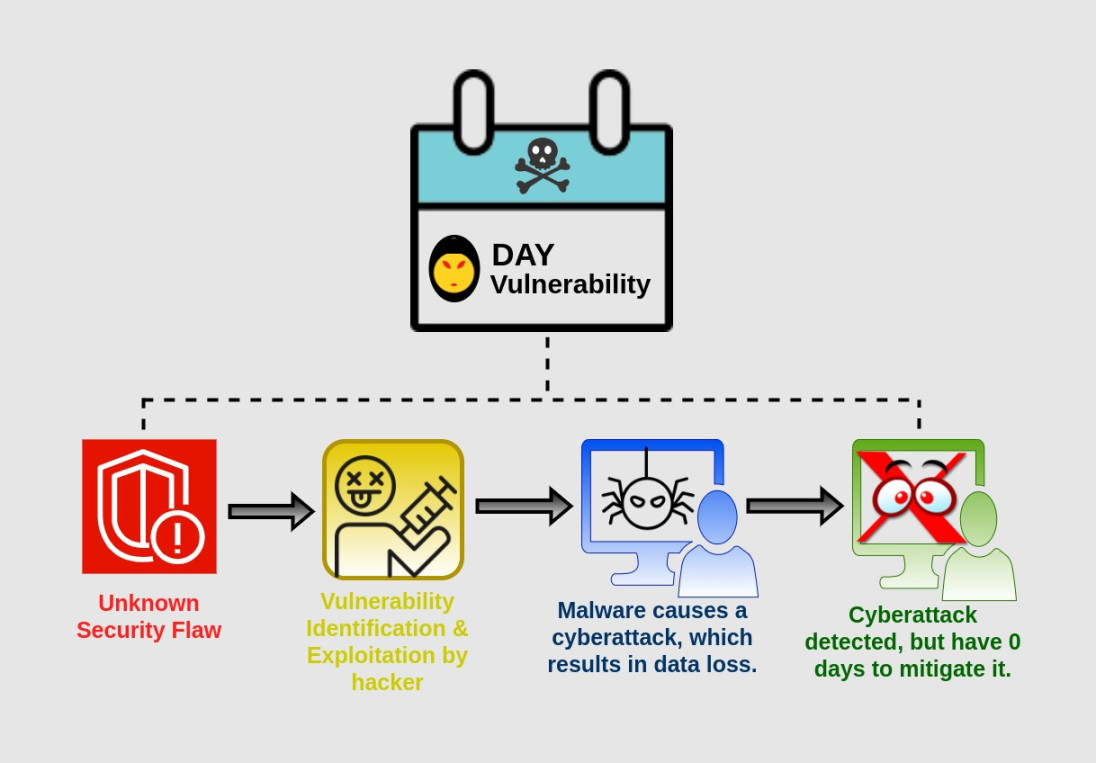
A zero-day exploit is a type of cyber attack that takes advantage of a security vulnerability in a software application before the developer has had a chance to patch it. In other words, it is an attack that occurs on day zero of the vulnerability being discovered. This gives the defender (in this case, the software developer) zero days to fix the vulnerability before it is exploited by hackers.
The concept of zero-day exploits may sound like something out of a spy movie, but in reality, they are a very real and potent threat in today’s digital world. Hackers use zero-day exploits to gain unauthorized access to systems, steal sensitive information, or disrupt services. Because the vulnerability is unknown to the software developer, zero-day exploits are extremely difficult to defend against.
So, how do hackers discover zero-day exploits in the first place? The truth is, it requires a combination of skill, patience, and a keen eye for detail. Hackers may spend hours or even days analyzing software code, looking for weaknesses that could be exploited. Once a vulnerability is found, the hacker can develop an exploit that takes advantage of it, giving them the ability to bypass security measures and gain access to a system.
Zero-day exploits can be used in a variety of ways, depending on the hacker’s goals. Some hackers may use them to steal valuable information, such as credit card numbers or personal data. Others may use them to disrupt services, like shutting down a website or a critical infrastructure system. In some cases, zero-day exploits have even been used as part of larger cyber attacks, such as ransomware campaigns or data breaches.
The impact of a zero-day exploit can be devastating, both for individuals and organizations. For individuals, a zero-day exploit could result in identity theft, financial loss, or invasion of privacy. For organizations, the consequences can be even more severe, ranging from financial damage to reputational harm. In extreme cases, a zero-day exploit could lead to a complete shutdown of operations, putting livelihoods at risk.
Despite the dangers of zero-day exploits, there are steps that individuals and organizations can take to protect themselves. Regularly updating software and operating systems can help to patch known vulnerabilities and reduce the risk of falling victim to a zero-day exploit. Using strong passwords, implementing multi-factor authentication, and being cautious when clicking on links or downloading attachments can also help to prevent cyber attacks.
In conclusion, zero-day exploits are a powerful and stealthy weapon in the arsenal of cybercriminals. By taking the time to understand how they work and implementing best practices for cybersecurity, individuals and organizations can better protect themselves against this ever-present threat. So, the next time you hear about a zero-day exploit in the news, you’ll know exactly what’s at stake in the high-stakes world of cybersecurity intrigue.
![What's the Best Authentication Method? Analysis []](https://rusterpedia.biz.id/wp-content/uploads/2024/10/what-s-the-best-authentication-method-analysis-60x60.png)


