Guarding Your Treasures: Tips for Proving Ownership
Do you have valuable items that you want to protect? Whether it’s jewelry, electronics, or family heirlooms, it’s important to have a way to prove that these items belong to you. In this article, we will explore some tips for proving ownership of your treasures and keeping them safe.
One of the easiest ways to prove ownership of your valuables is to keep detailed records. This can include receipts, appraisals, and photographs of the items. Having documentation that shows when and where you purchased the item can be crucial in proving ownership in case of theft or loss. Make sure to keep these records in a safe place, such as a locked filing cabinet or a safe deposit box.

Another important tip for proving ownership is to engrave or mark your items with a unique identifier. This could be your name, initials, or a serial number. By marking your items, you can easily prove that they belong to you if they are ever stolen or misplaced. You can also consider registering your valuables with a national database, such as the National Property Register, to help authorities identify and return your items if they are recovered.
In addition to keeping records and marking your items, it’s also a good idea to create a home inventory. This can be a list or spreadsheet that details all of your valuable possessions, including descriptions, serial numbers, and photographs. In the event of a burglary or natural disaster, having a home inventory can help you prove ownership to your insurance company and make the claims process smoother.
It’s also important to consider storing your valuables in a secure location. This could be a safe at home, a safe deposit box at a bank, or a secure storage facility. Make sure to choose a storage option that is fireproof and waterproof to protect your items from damage. Additionally, consider installing a security system in your home to deter burglars and protect your treasures.
When it comes to proving ownership of your treasures, it’s important to stay proactive and vigilant. Regularly review your records and update your home inventory as needed. If you purchase new items, make sure to add them to your documentation. By taking these steps, you can protect your valuables and have peace of mind knowing that you can prove ownership if the need arises.
In conclusion, guarding your treasures and proving ownership is essential for keeping your valuables safe. By keeping detailed records, marking your items, creating a home inventory, and storing your valuables in a secure location, you can protect your treasures and prove ownership in case of loss or theft. Stay proactive and diligent in safeguarding your valuables, and you can enjoy peace of mind knowing that your treasures are protected.
Stay Secure, Stay Safe: Verifying Your Identity
In today’s digital age, it’s more important than ever to protect your identity and prove that you are who you say you are. With the rise of cybercrime and identity theft, verifying your identity has become a crucial step in keeping your personal information safe. Whether you’re accessing your bank account online, applying for a new job, or even just signing up for a new social media account, proving your identity is essential.
One of the most common ways to verify your identity is through the use of official identification documents. These can include things like your driver’s license, passport, or social security card. These documents typically have unique identification numbers or barcodes that can be scanned or entered into a system to confirm your identity. It’s important to keep these documents safe and secure, as they are often required for important transactions or interactions.
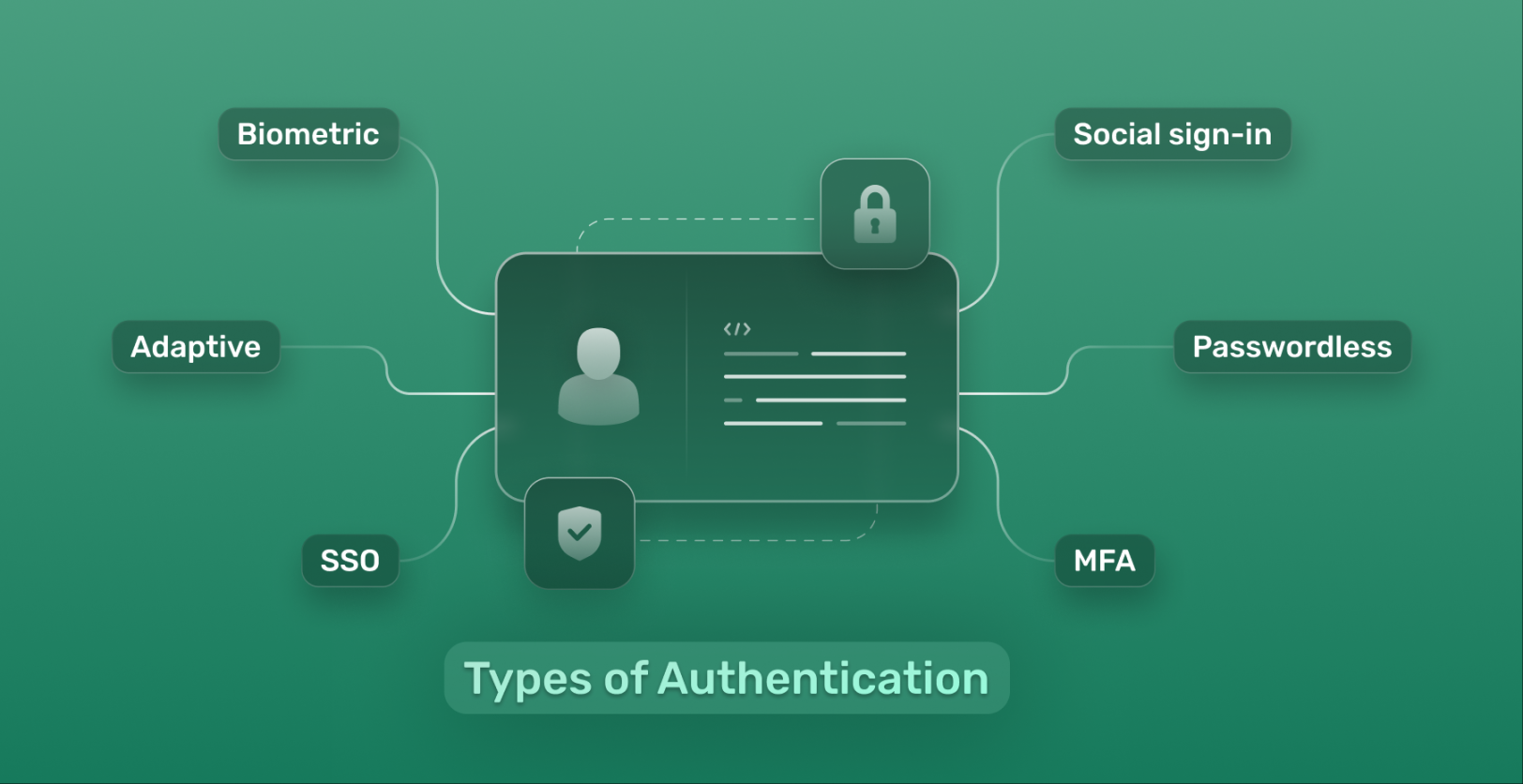
Another way to verify your identity is through the use of biometric data. This can include things like fingerprint scans, facial recognition technology, or even voice recognition. Biometric data is unique to each individual and can be difficult for fraudsters to replicate. Many smartphones and other devices now come equipped with biometric sensors for added security.
In addition to official documents and biometric data, another way to verify your identity is through the use of security questions and passwords. When setting up an account online, you may be asked to choose security questions that only you would know the answers to. This can help to confirm your identity if you ever forget your password or need to reset your account. It’s important to choose security questions that are not easily guessable by others.
Passwords are another important aspect of verifying your identity online. It’s crucial to choose strong, unique passwords for each of your accounts to prevent hackers from gaining access to your personal information. Avoid using easily guessable passwords like password123 or 123456, and consider using a password manager to keep track of all your different passwords.
One more way to verify your identity is through the use of two-factor authentication. This adds an extra layer of security by requiring you to enter a code sent to your phone or email in addition to your password. Two-factor authentication can help to prevent unauthorized access to your accounts, even if someone has your password.
When it comes to verifying your identity in person, there are a few additional steps you can take. For example, you may be asked to provide a photo ID when purchasing alcohol or tobacco products, or when entering certain establishments. It’s important to always carry a valid form of identification with you, especially when traveling or engaging in age-restricted activities.
Overall, verifying your identity is a crucial step in keeping your personal information safe and secure. By using a combination of official documents, biometric data, security questions, passwords, and two-factor authentication, you can help to protect yourself from identity theft and fraud. Remember to always keep your identification documents safe and secure, and never share your passwords or security information with anyone else. Stay secure, stay safe, and keep proving that you are who you say you are.



